Virtual Private Network Enhances Remote Collaboration
Updated: 10 Jan 2025
10
A Virtual Private Network (VPN) is a technology that allows you to create a secure, private connection over a less secure public network, such as the internet. VPNs encrypt your data and hide your IP address, ensuring that your online activities remain private, secure, and anonymous. VPNs are essential for protecting sensitive information when using public Wi-Fi, bypassing geographical restrictions, and securing corporate communication in remote work environments.
1. What is a Virtual Private Network ?
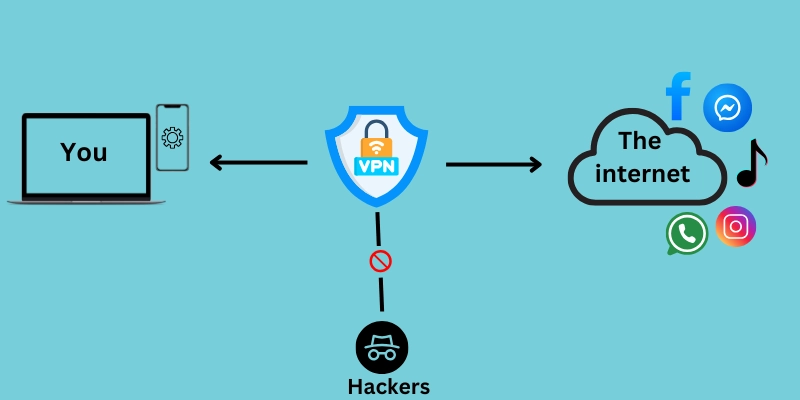
A Virtual Private Network (VPN) is a secure connection between a user’s device (like a computer or smartphone) and a remote server, which acts as a gateway to the internet. By using encryption and tunneling protocols, a VPN ensures that the data transmitted between your device and the server is private and secure, even when you’re accessing it through a public network.
The primary function of a VPN is to protect your data from hackers, prevent tracking of your online activities, and allow you to appear as if you’re accessing the internet from a different location. Whether you’re working remotely, accessing sensitive data, or simply trying to browse the web privately, a VPN plays a crucial role in ensuring your security.
Example: Think of a VPN as a tunnel that connects your device to the internet, where the tunnel protects your data and keeps it hidden from potential threats.
2. How Does a VPN Work?
A VPN works by creating a secure, encrypted “tunnel” between your device and a remote server. This tunnel prevents anyone (e.g., hackers, ISPs, government agencies) from intercepting or snooping on your data. Here’s how it typically works:
- Encryption: When you connect to a VPN, it encrypts all your internet traffic. This means that even if someone were to intercept your connection, they would only see scrambled data that’s impossible to read without the decryption key.
- Tunneling: The VPN establishes a secure tunnel between your device and a VPN server. This tunnel carries your internet traffic securely from your device to the VPN server, which then forwards your traffic to the desired destination (like a website or app).
- IP Masking: Your real IP address is masked by the VPN server’s IP address. This makes it appear as if you are accessing the internet from the location of the VPN server, rather than your actual physical location. This helps with privacy and can also bypass geographical restrictions.
- Decryption: When your encrypted data reaches the VPN server, it is decrypted and forwarded to its final destination (like a website). The process is reversed when the data returns to you.
3. Types of VPNs
There are several different types of VPNs, each designed for specific use cases. The two most common types of VPNs are Remote Access VPNs and Site-to-Site VPNs. Additionally, there are various protocols that these VPNs use for encryption and security.
Remote Access VPN
A Remote Access VPN is primarily used by individuals to securely connect to a remote network (such as a company network or a home network) from a different location. This is the most common type of VPN used by individuals, especially for remote work, accessing blocked content, or maintaining privacy when using public Wi-Fi.
- Use Case: Remote employees can use a Remote Access VPN to securely access their company’s internal network and resources (such as email, files, or applications) from any location.
- Example: A freelance writer uses a VPN to connect to their office network, allowing them to access work files securely from a coffee shop.
Site-to-Site VPN
A Site-to-Site VPN is used to connect two or more different networks, usually in separate geographical locations, so that devices in those networks can communicate as if they are part of the same local network. This type of VPN is typically used by businesses with multiple offices or branches.
- Use Case: A company with offices in New York and London can set up a Site-to-Site VPN to ensure that employees in both locations can securely access shared resources (such as databases or internal websites).
- Example: A multinational company uses a Site-to-Site VPN to connect its headquarters in the US with its remote office in Asia.
Client-to-Server VPN
A Client-to-Server VPN is used when a single device (client) connects to a remote server, usually for purposes such as browsing securely, accessing data, or using a specific app.
- Use Case: When an employee connects their laptop to a company’s private network through a VPN while traveling, this type of connection is being used.
4. VPN Protocols
VPNs use various encryption protocols to ensure secure communication between your device and the VPN server. These protocols define how the VPN connection is established, how data is encrypted, and how information is transmitted securely.
OpenVPN
OpenVPN is one of the most popular and secure VPN protocols. It uses SSL/TLS encryption to create a secure tunnel and supports both UDP and TCP connections. OpenVPN is open-source, which means it is free to use and can be audited for security.
- Pros: High security, open-source, flexible.
- Cons: Can be slower than other protocols due to heavy encryption.
IKEv2/IPSec
IKEv2 (Internet Key Exchange version 2) is a fast and secure protocol commonly used in modern VPN services. It pairs with IPSec for encryption and is particularly known for its speed and stability, especially when switching between networks (e.g., from Wi-Fi to mobile data).
- Pros: Fast, reliable, supports mobile devices well.
- Cons: Less flexible than OpenVPN in terms of configuration.
L2TP/IPSec
L2TP (Layer 2 Tunneling Protocol) is often paired with IPSec for encryption. L2TP itself doesn’t offer encryption, but when combined with IPSec, it provides a secure connection. It’s commonly used when OpenVPN or IKEv2 isn’t available.
- Pros: Secure with IPSec, easy to set up.
- Cons: Slower compared to OpenVPN and IKEv2.
PPTP
PPTP (Point-to-Point Tunneling Protocol) is one of the oldest VPN protocols, and while it is very fast, it offers weak encryption and has numerous security vulnerabilities. It’s no longer recommended for secure communications but might still be used in situations where speed is the primary concern and security is less of a priority.
- Pros: Fast connection speeds.
- Cons: Weak encryption, not recommended for secure applications.
Wire Guard
Wire Guard is a newer VPN protocol designed to be faster and simpler than existing protocols. It aims to provide better security with less complexity. It’s gaining popularity for its efficiency and speed.
- Pros: Very fast, efficient, easy to configure.
- Cons: Still relatively new, may not be as widely supported as others.

5. Benefits of Using a VPN
A VPN provides multiple advantages, particularly in terms of privacy, security, and accessibility. Here are some of the key benefits of using a VPN:
- Privacy and Anonymity: By masking your real IP address, a VPN ensures that your online activities remain private. This is essential for protecting your identity and preventing third-party tracking.
- Enhanced Security: VPNs use encryption to secure your internet traffic, making it difficult for hackers, ISPs, or other parties to intercept or steal your data. This is particularly important when using public Wi-Fi networks.
- Access Geo-Restricted Content: Many streaming services (like Netflix, Hulu, or BBC iPlayer) restrict content based on your location. A VPN allows you to bypass these restrictions by connecting to a server in a different country.
- Bypass Censorship: In countries with strict internet censorship (such as China or the UAE), a VPN can help you access blocked websites and services by masking your location and encrypting your connection.
- Secure Remote Access: VPNs are essential for employees working remotely, providing them secure access to their company’s internal networks and resources.
6. Common Uses of VPNs
- Remote Work: Employees use VPNs to securely access their company’s internal network and systems when working from home or traveling.
- Secure Online Banking: VPNs ensure that your sensitive financial data is protected when using online banking services, especially when accessing these services on public Wi-Fi networks.
- Bypass Content Restrictions: VPNs allow users to access content that may be restricted or unavailable in their region, such as watching international Netflix libraries or accessing social media platforms in censored countries.
- Enhanced Online Privacy: VPNs can prevent websites from tracking your online activities, thereby protecting your privacy and reducing the risk of being targeted by ads.
7. Setting Up a VPN
Setting up a VPN is relatively simple, and you can do it in several ways, depending on your needs.
- Choose a VPN Provider: Select a VPN provider that meets your needs (e.g., security, speed, price). Popular VPN providers include ExpressVPN, NordVPN, and CyberGhost.
- Download and Install the VPN Software: Once you choose a provider, download and install their VPN software or app on your device (computer, smartphone, etc.).
- Log In and Connect: After installation, log in with your VPN account credentials and connect to a server of your choice. You can select the location from which you want to appear as browsing.
- Adjust Settings: Some VPN services allow you to customize encryption settings, choose specific VPN protocols, and set up automatic connections for enhanced security.
8. Troubleshooting Common VPN Issues
While VPNs are reliable, you may encounter issues that require troubleshooting:
- Slow Connection Speeds: This can happen if the VPN server you are connected to is far away or if the server is overloaded. Try connecting to a closer server or switching to a less congested server.
- Connection Drops: If your VPN connection is frequently dropping, try switching protocols (e.g., from IKEv2 to OpenVPN) or updating your VPN software.
- Unable to Access Certain Websites: Some websites may block VPN traffic. Try connecting to a different server or use a VPN service with obfuscation features that disguise VPN traffic.
9. Tips for Using a VPN
- Choose a Reliable VPN Provider: Not all VPNs are created equal. Select a provider with a proven track record of privacy and security.
- Use Strong Encryption: Ensure your VPN uses robust encryption standards like AES-256 for maximum security.
- Test Speed Regularly: VPNs can slow down your internet speed, so regularly test and choose servers that offer the best performance for your needs.
Is using a VPN legal?
Yes, using a VPN is legal in most countries. However, some countries have restrictions on VPN use, especially when used to bypass censorship or illegal activities.
Does VPN make internet faster?
A VPN generally does not make the internet faster. In fact, it can sometimes slow down your connection due to the encryption process and the routing of data through remote servers. However, in some cases, a VPN might help improve speeds by bypassing network throttling (when an internet service provider intentionally slows down your connection) or accessing faster servers. Overall, the impact on speed varies depending on the VPN service, server location, and internet conditions.
Can I use a VPN on mobile devices?
Yes, most VPN providers offer apps for mobile devices, allowing you to secure your internet connection on smartphones and tablets.
What is VPN used for?
A VPN (Virtual Private Network) is used to create a secure, encrypted connection between a user’s device and the internet, protecting data from potential threats. It allows users to access restricted content by masking their IP address, making them appear to be in a different location. VPNs are commonly used for privacy, security, and bypassing geographic restrictions on websites or services.
Does a VPN make me completely anonymous online?
While a VPN provides strong privacy protection, it doesn’t make you completely anonymous. Other factors, such as cookies or personal information shared online, can still be tracked.
Conclusion
A Virtual Private Network is an essential tool for anyone looking to protect their privacy, enhance security, and bypass internet restrictions. Whether you’re browsing the internet, accessing corporate resources remotely, or streaming content from other countries, a VPN ensures your online activities are secure and anonymous. With various types, protocols, and benefits, VPNs provide a versatile solution for personal and professional use in today’s interconnected world.
Please Write Your Comments